With the prevalence of email spam, if you are running a VPS that processes mail you may encounter issues with spam. If have received an abuse notification, then there is an issue that needs to be addressed.
This article provides some advice that you can use to start investigating these issues.
If you have been sent the mail headers for the spam look for the last ‘Received’ line, an example is below.
Received: from [172.18.5.9] (port=4637 helo=User)
by your.server.example with esmtpa (Exim 4.82)
(envelope-from <[email protected]>)
id 2XFVHL-100459-5R; Fri, 15 Aug 2014 07:31:07 +1000
In this example we can see that someone from 172.18.5.9 has connected to ‘your.server.example’. If this is in fact your server then it is certain that the spam has been sent using your server. If it is not your server, and you can see your email address in the ‘envelope from’ section, then it is likely that the spammer is pretending to send from your email address.
If the spam is originating from your server there are a few ways this can be confirmed and investigated. Using cPanel you can use the ‘Mail Delivery Reports‘ tool to find out how the email was sent. Below are some steps you can follow to do this.
1.Access WHM by browsing to the link sent in your welcome email
2.Login using the details provided in the welcome email
3. You will now see the home screen of WHM
4. The quickest way to bring up the ‘Mail Delivery Reports‘ page is to search for ‘reports’ in the search bar
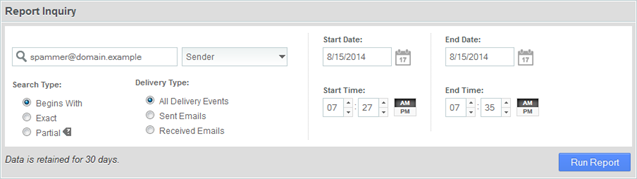
5. One you have the page open you can enter search criteria to locate the spam, click the blue ‘Run Report‘ button to start the search
6. Once the email has been located, click on the magnifying glass icon on the far right
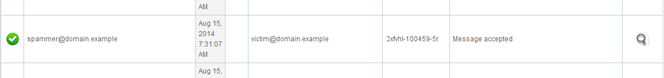
7. This will bring up more detailed information about the email
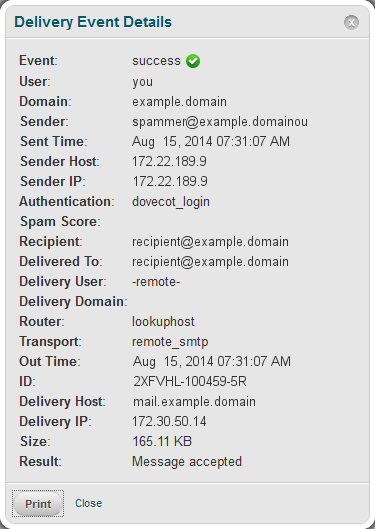
- In this example the email was sent by the ‘you’ user, since this was authenticated by dovecot it shows the ‘you’ user’s login details are compromised.
- If the user is ‘nobody’ or ‘apache’ and the sender IP is the server itself or 127.0.0.1 that indicates the email was sent via a web form.
With this information you can track down the source of the spam email and know what kind of action you need to take to prevent it.
In the case of compromised user accounts, resetting the password to a new, strong password and having the user scan their systems for malware will resolve most issues.
In the case of website forms, you will need to track down which account it originated from. You can use maldet to locate the account, we are able to install this for you if needed. Once the account has been identified the person responsible for the site will most likely need to update the website software. We recommend contacting your Website’s Developer.